According to Forbes Advisor, there were 2,365 cyberattacks in 2023, affecting an astounding 343,338,964 people — roughly 10 million more people than the U.S. population. A USA Today article says “the cost of cybercrime would reach a massive $9.5 trillion in 2024 and exceed $10.5 trillion in 2025,” and it “is estimated that attacks on businesses, consumers, governments and devices will happen every two seconds by 2031.” With the average data breach costing companies $4.5 million as rapidly evolving technologies make cyber attackers more sophisticated by the day, this isn’t a concern anyone has the luxury of ignoring.
Along with the crucial efforts to mitigate the effects of climate change and severe weather events, an aging infrastructure and an aging workforce, and the mandate to keep up with environmental regulations, utilities are working diligently to protect their communities from the added threat of cyberattacks. To safeguard their communities and ensure they can continue to provide essential services, utility companies are taking proactive measures to protect against these cyber threats. While addressing climate change and environmental issues remains a top priority, utilities recognize that cybersecurity is a critical component of their overall strategy.
With cyberattacks becoming increasingly sophisticated and frequent, utilities must remain vigilant in their efforts to protect their systems and data. Failure to do so could result in significant disruptions to services and potentially devastating consequences for the communities they serve.
Black & Veatch’s 2024 Electric Report illustrates the pressing need for investment in cybersecurity across both information technology (IT) and operational technology (OT).
On the IT side, seven in 10 survey respondents consider phishing attacks as their most concerning cyberthreat, followed by ransomware and malware (both at 45 percent) — three methods that tend to dominate headlines. On the OT front, malware (52 percent) and ransomware (47 percent) top the list, with cloud vulnerabilities coming in as a most concerning threat for 35 percent of respondents.
While no defense is invincible, ample solutions exist to increase agility for IT and OT defenses.
One question remains: How exactly is cybersecurity affecting OT?
Measuring Preparedness
The rate of attacks on OT is far outpacing the maturity of most industrial cybersecurity programs. As systems become more connected and automated, they become more exposed to increasingly skilled cyber attackers. Meanwhile, many OT managers don’t have a comprehensive view of their networks, leaving them even more vulnerable.
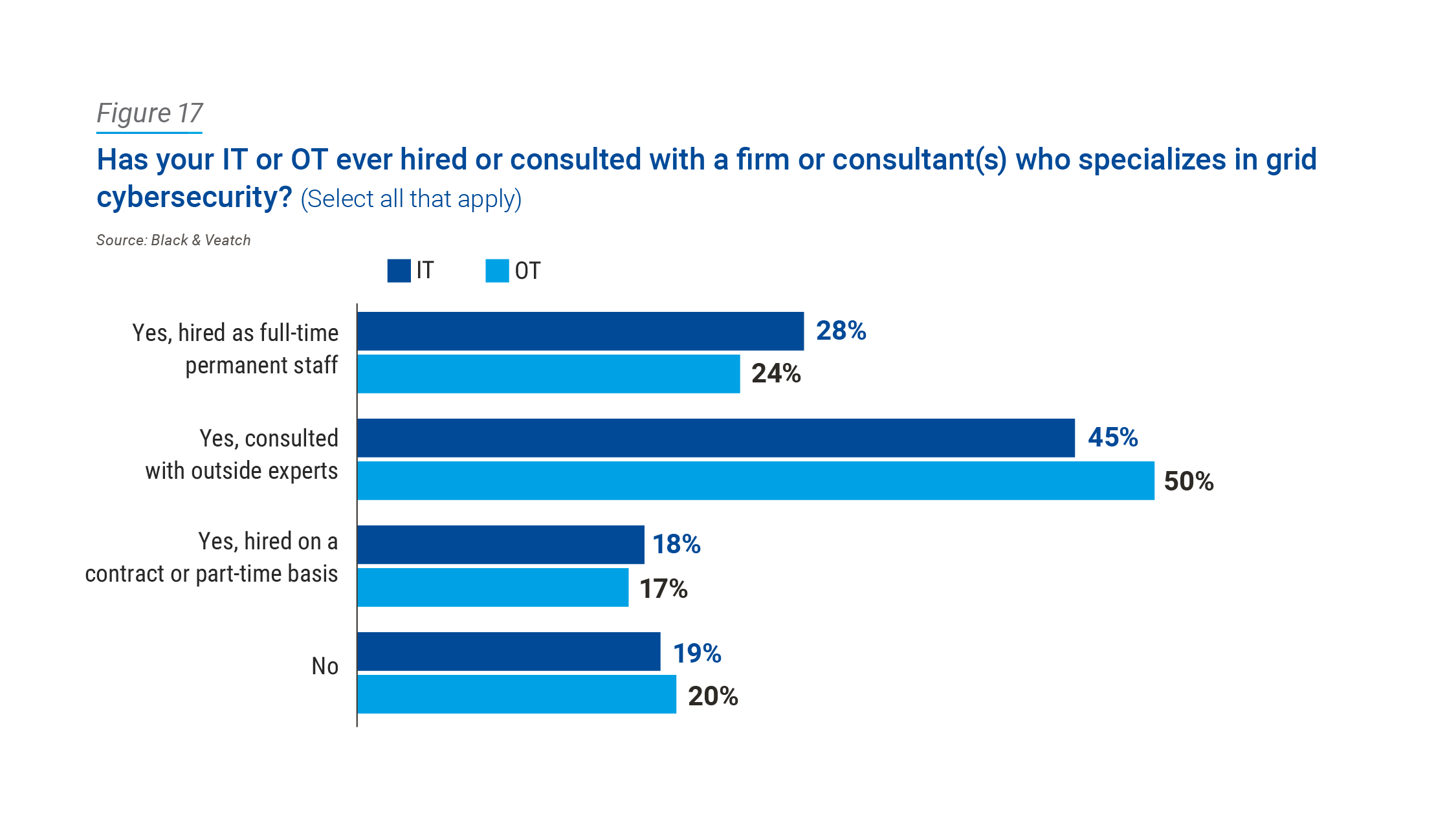
This translates to the pressing dilemma: most utilities’ cybersecurity protection plans are too immature to protect their OT assets from cyber threats. When asked if their utility has ever hired or consulted with an external, specialized cybersecurity firm, only one-quarter of survey respondents reported having full-time permanent staff. An additional half of those surveyed responded that they have consulted with outside cybersecurity consultants such as companies like Black & Veatch (Figure 17). While that is good, that also means half have never consulted with an outside expert, leaving them and the public’s access to electricity potentially vulnerable to threats.
One-fifth of respondents have never hired or consulted with grid cybersecurity specialists — a concerning number, given the gravity of the threat.
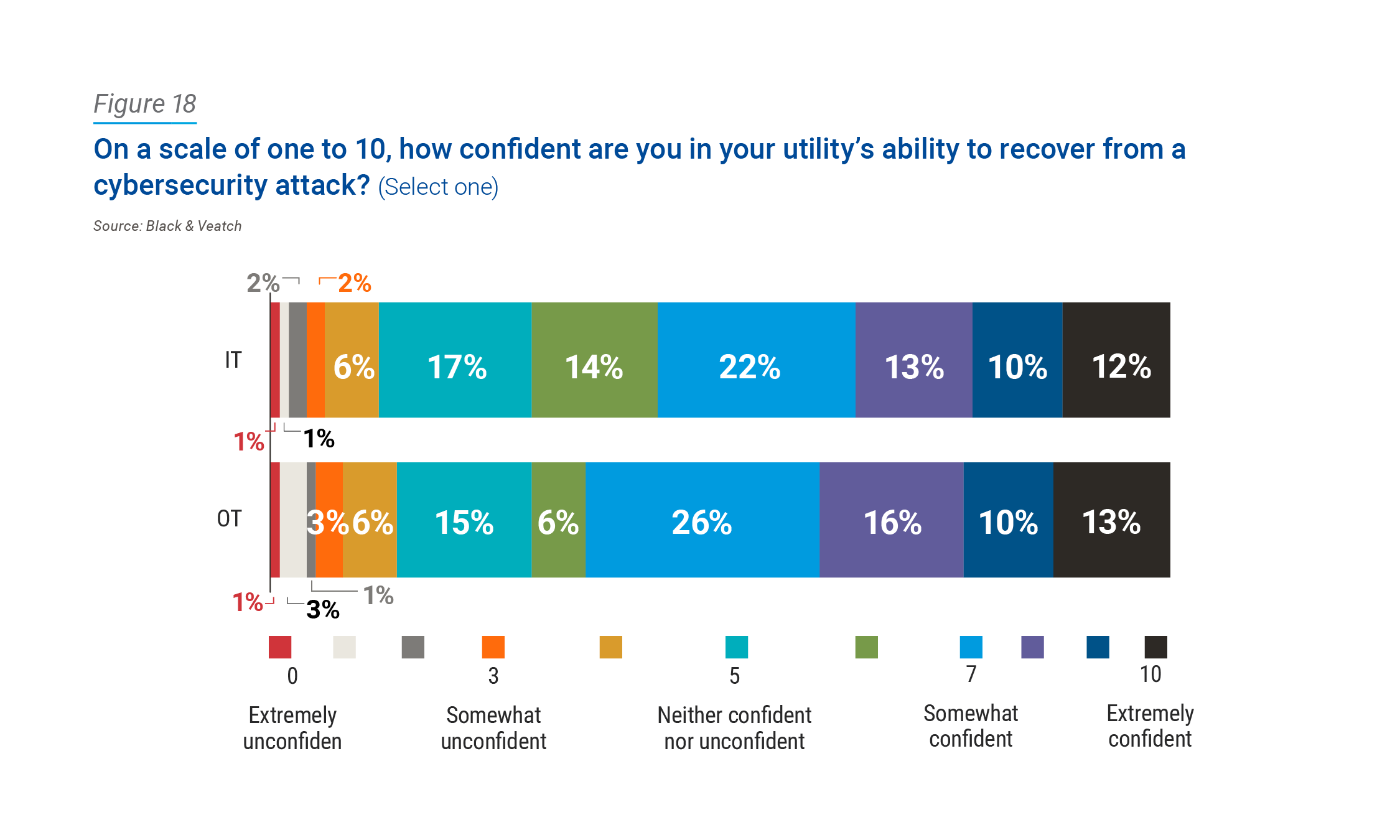
The survey shows a level of confidence in resilience should an attack take place. On the IT side, seven in 10 respondents reported some level of confidence, with 12 percent casting themselves as “extremely confident.” Those numbers virtually mirror the sentiment on the OT side, where 71 percent express some level of confidence and 13 percent say they’re extremely confident (Figure 18).
The figures at hand paint a picture of an industry ready and armed for a cyberattack, but the question remains: could they withstand just any cyberattack? Additionally, recovery might be an objective assurance, but the length at which it takes to recover becomes a subjective matter, requiring more context around the utility’s specific plans.
Since the attackers are becoming more sophisticated, it is especially crucial for utilities to prepare and have a plan and resources in place for a speedy recovery that minimizes the number of households and businesses affected.
Compliance as a Starting Point
The industry is on the precipice of big changes to meet regulatory standards in the constantly evolving energy ecosystem. But compliance alone might be the go-to standard for a far greater number than the industry should feel comfortable with.
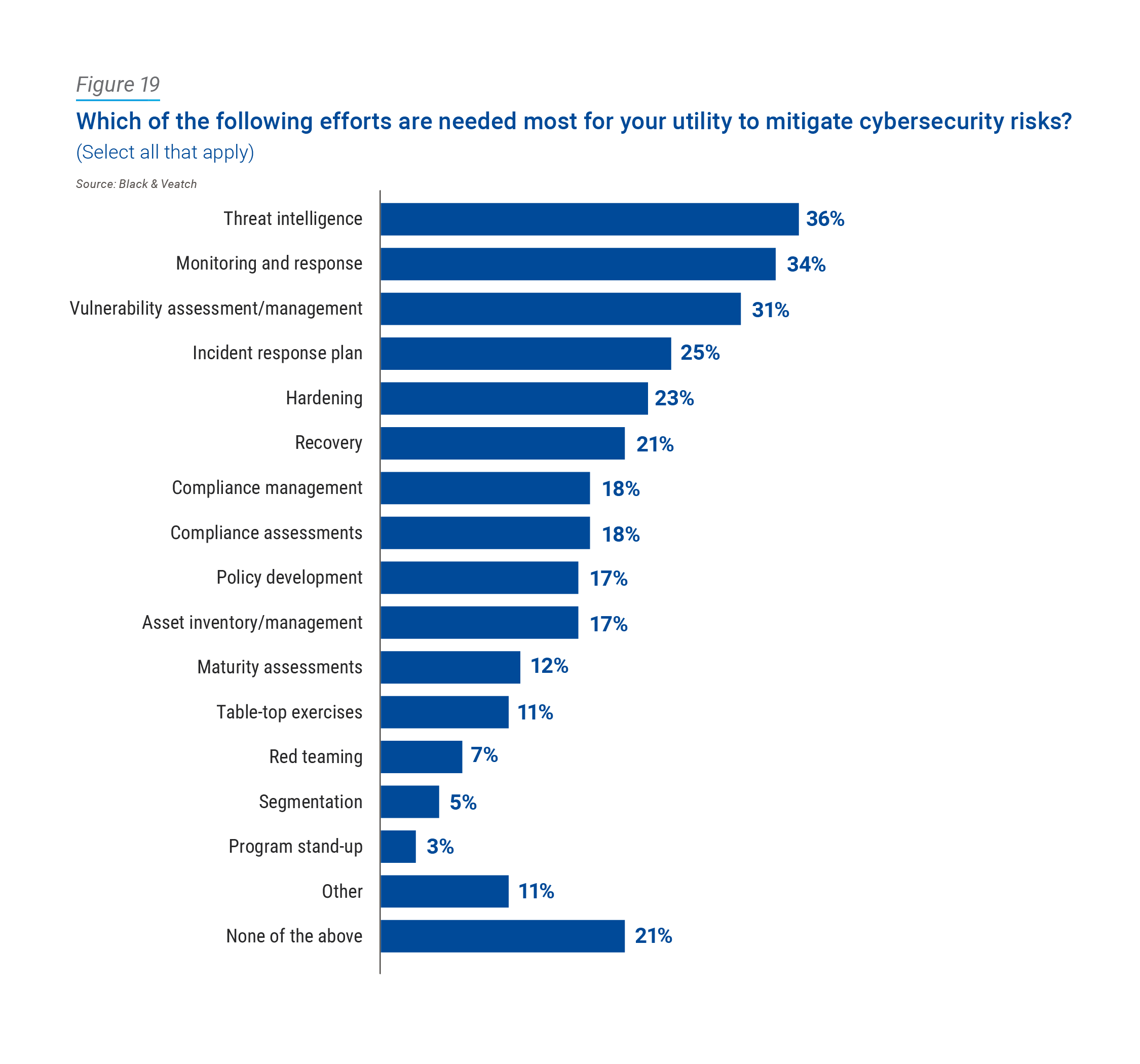
When asked to identify what efforts are needed most by their utility to better mitigate cyber risks, 36 percent pointed to threat intelligence, followed by monitoring and response (34 percent) and vulnerability assessments and management (31 percent) (Figure 19).
With 18 percent of respondents under the impression that compliance is most needed for their utility, it should be clarified: compliance alone is not enough. An organization can be fully compliant and not very secure at all. By its nature, compliance is a lowest common
denominator game, often casting a false sense of security. The industry is replete with stories of the fully compliant getting taken down by cyberattacks.
While mere compliance is part of the equation, for almost one-fifth of respondents to answer it as the most needed response shows a disconnect in where we are in the electric industry versus where we need to be.
In this real-life game of chess, utilities would be wise to not conflate compliance with actual security — or see it as merely a box-checking exercise. It’s essential for utilities to ensure that their cyber defenses are robust, thoroughly implemented, consistently monitored, and frequently pressure-tested and revised to remain effective. As threats evolve, so must the protections against them.
Think of it this way: In a neighborhood where most homes have a security alarm, those complemented with ample lighting, warning signs and a gated fence are less likely to be targets.








